15 Cybersecurity Resolutions Every SME
Must Adopt Before 2025 (Cybersecurity Tips for SME)

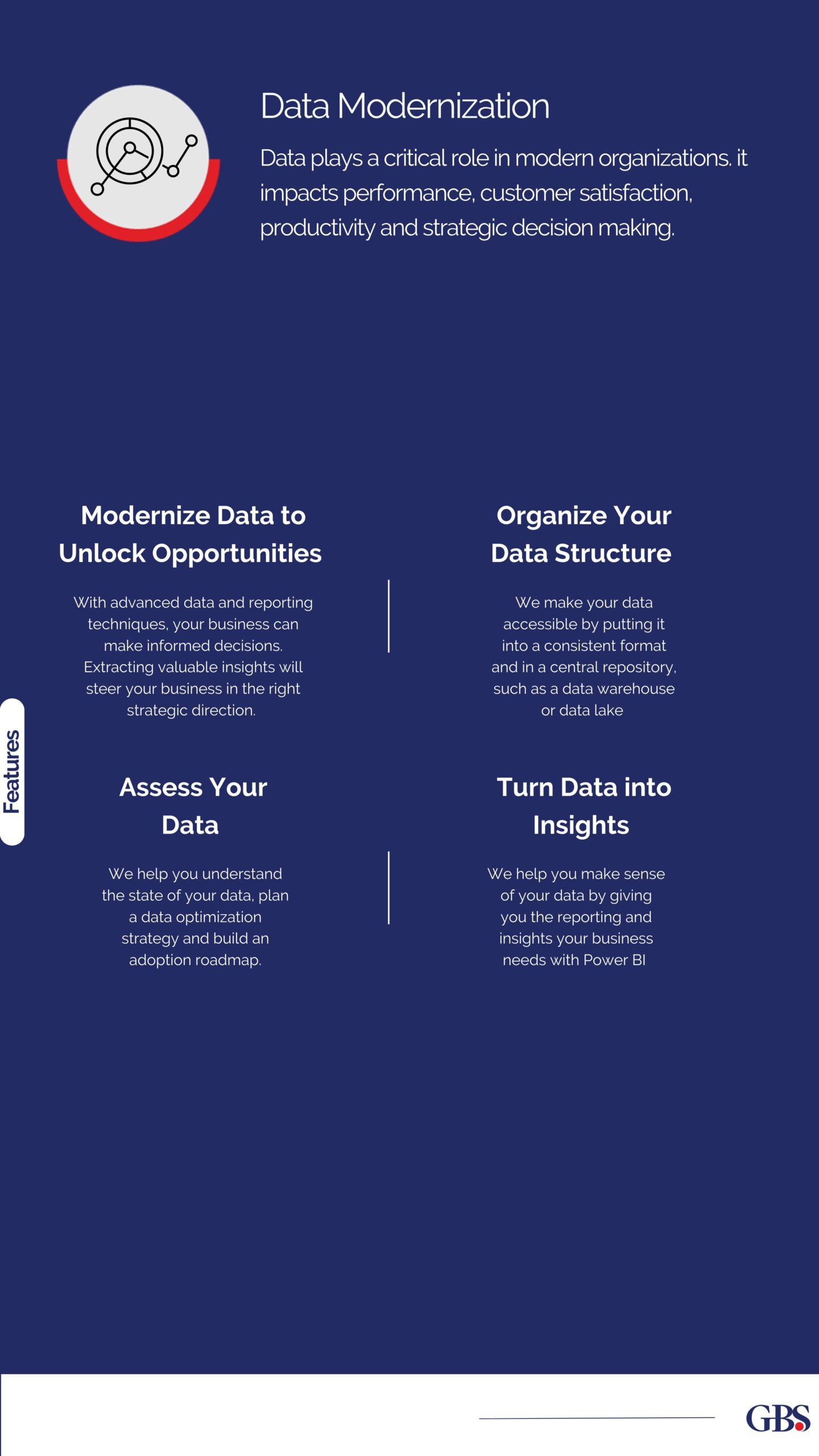
As 2024 draws to a close, small and medium enterprises (SMEs) face a critical decision: enter 2025 vulnerable to evolving cyber threats or step up their defenses to secure their future. Cyberattacks are becoming more sophisticated, and SMEs often lack the robust defenses of larger organizations, making them prime targets. Proactive measures aren’t just a choice—they’re a necessity to protect sensitive data, maintain customer trust, and ensure business resilience. Our list of Cybersecurity Tips for SME provide a comprehensive solution that can help you secure your business.
Before the new year begins, make cybersecurity a priority. The 15 essential Cybersecurity Tips for SMEs are curated by GBS—a leading cybersecurity provider in the Middle East—will help you safeguard your digital assets and set your business up for a secure and successful 2025.
Now Let’s Explore 15 Essential Cybersecurity Must Haves for SMEs in 2025
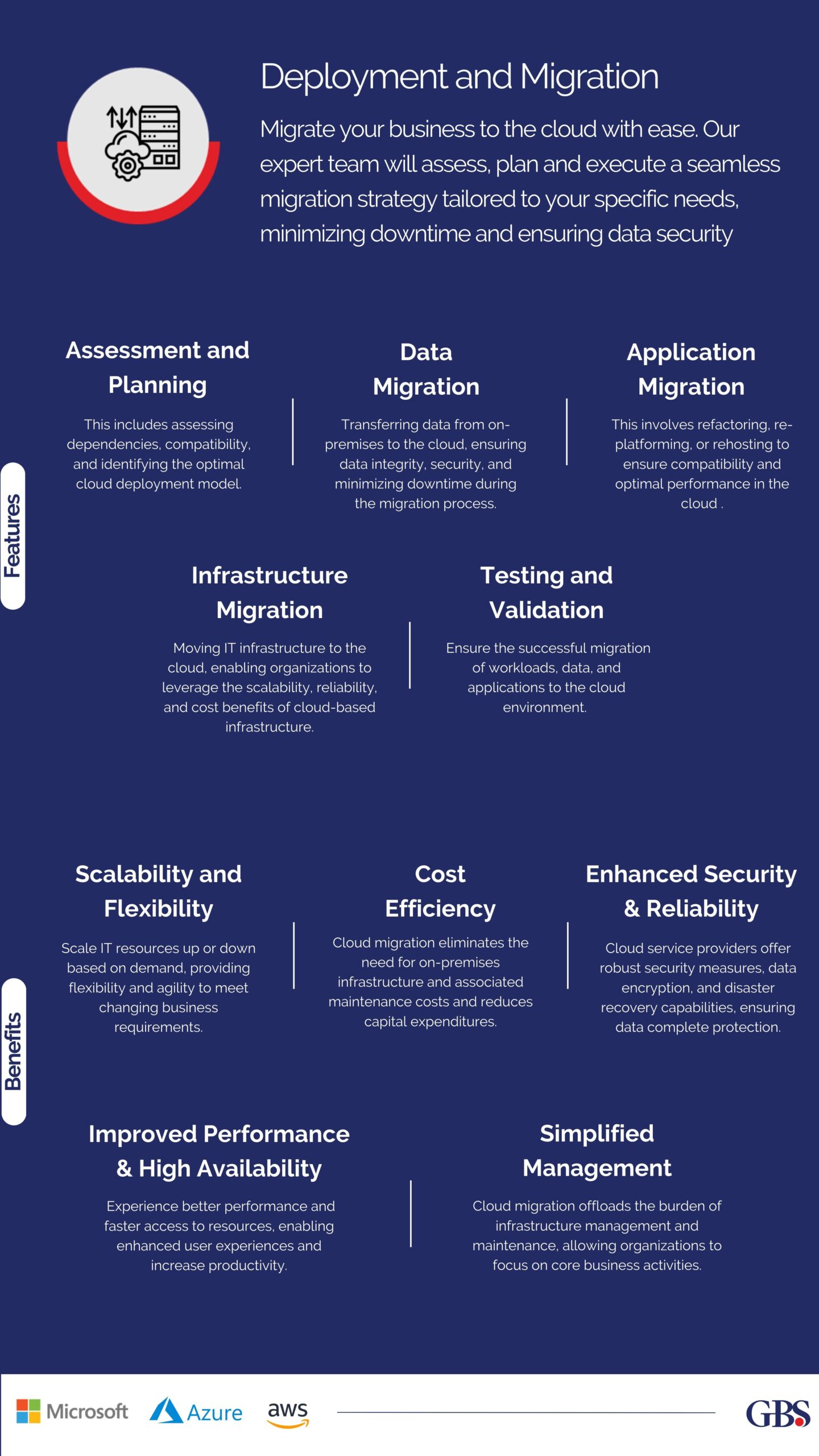
1. Educate and Train Employees –
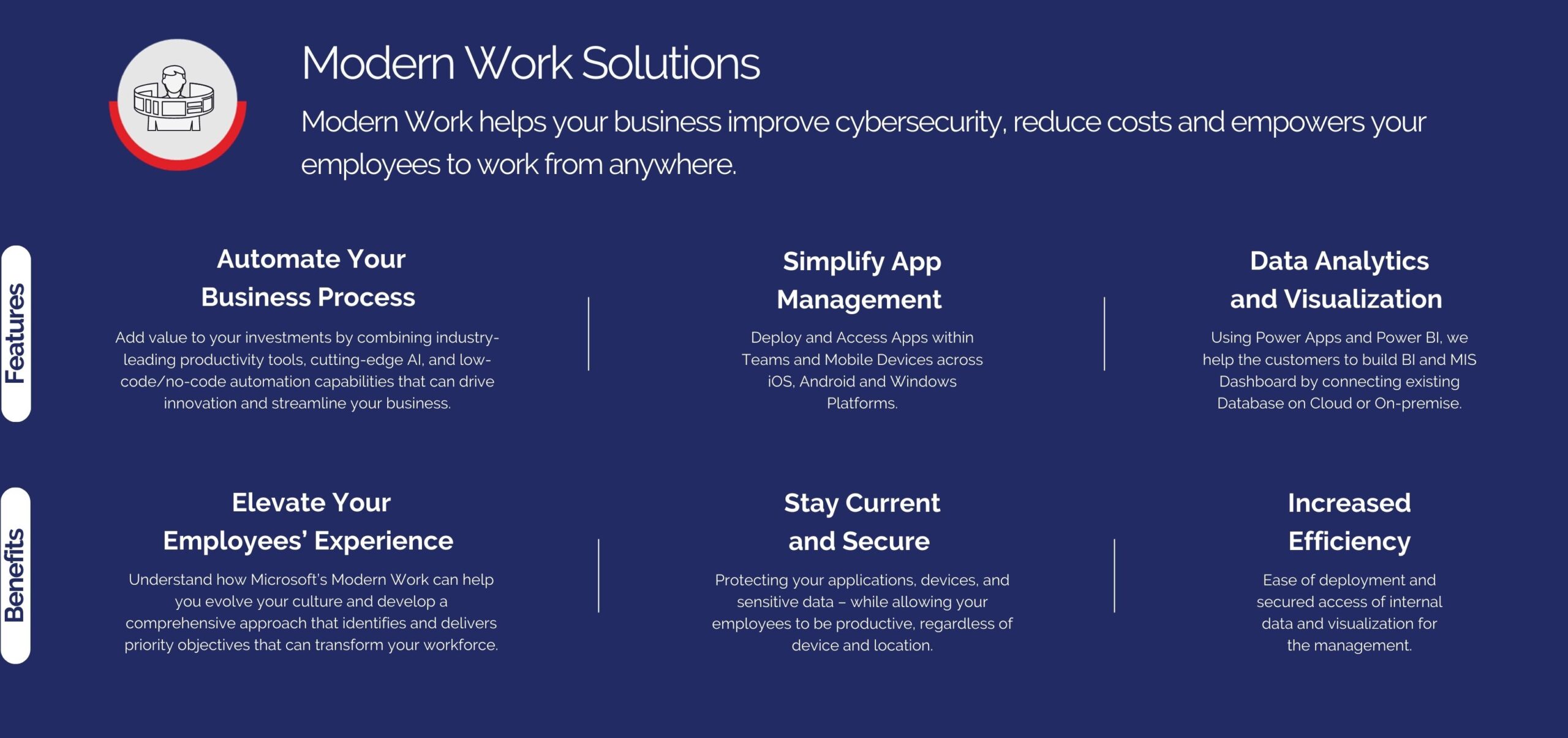
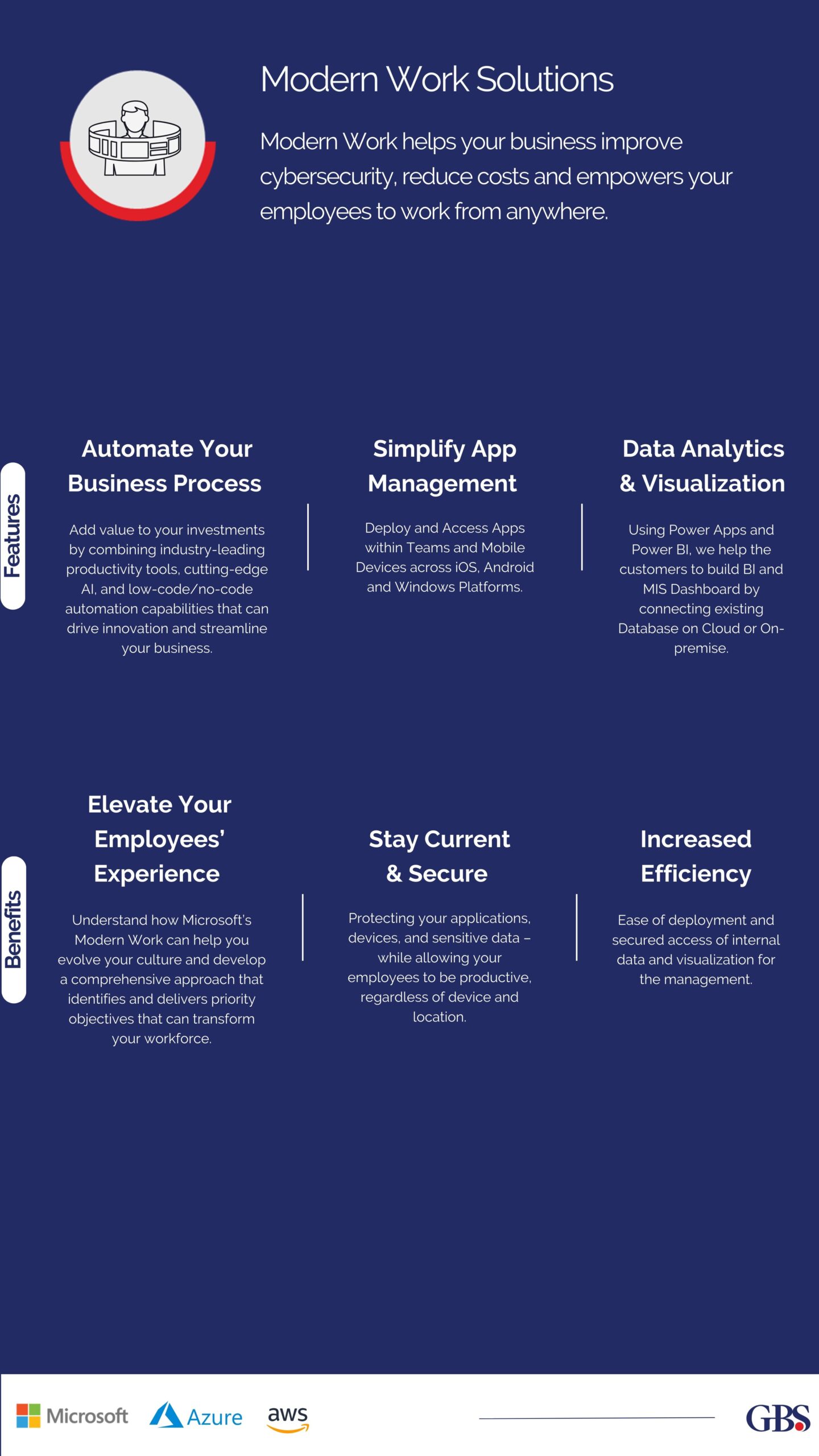
- The first line of defense against cyber attacks is your workforce. Regularly train them on cybersecurity best practices, such as recognizing phishing emails, using strong passwords, and reporting suspicious activities.
- An informed workforce can significantly reduce the risk of a successful cyber attack. Infrastructure management is the base of managed services, including network management, server maintenance, data center operations, and disaster recovery.
2. Implement Strong Password Policies –
- Ensure that all employees use strong, unique passwords for their accounts. Passwords should be at least 12 characters long and include a mix of letters, numbers, and symbols. GBS offers the best solutions and always encourages the use of password managers to securely store and generate complex passwords to cloud solutions offers benefits, like versatility and cost-effectiveness.
- Managed cloud services may help you plan, depart, maintain, and optimize your cloud infrastructure. Managed cloud services ensure smooth cloud use and adoption. Providers administer cloud infrastructure (IaaS) such as Azure or AWS and also move and optimize apps (SaaS). If you’re considering a cloud migration strategy or wish to use technology, this managed solution is for you.
3. Enable Multi-Factor Authentication (MFA) –
- Multi-factor authentication adds security by requiring users to provide at least two verification factors to access their account. This makes it much more difficult for attackers to gain unauthorized access, even if they have stolen the ids or passwords.
4. Keep Software and Systems Updated –
- Regularly update all software, operating systems, and applications to the latest versions. These updates often include security patches that fix vulnerabilities that cybercriminals could exploit. Enable automatic updates wherever possible to ensure you are always protected.
5. Use Antivirus and Anti-Malware Software –
- Install reputable antivirus and anti-malware software on all company devices. These tools can detect and remove malicious software that can compromise your systems. Keep these programs updated and ensure they work accurately to defend against the latest cyber threats.
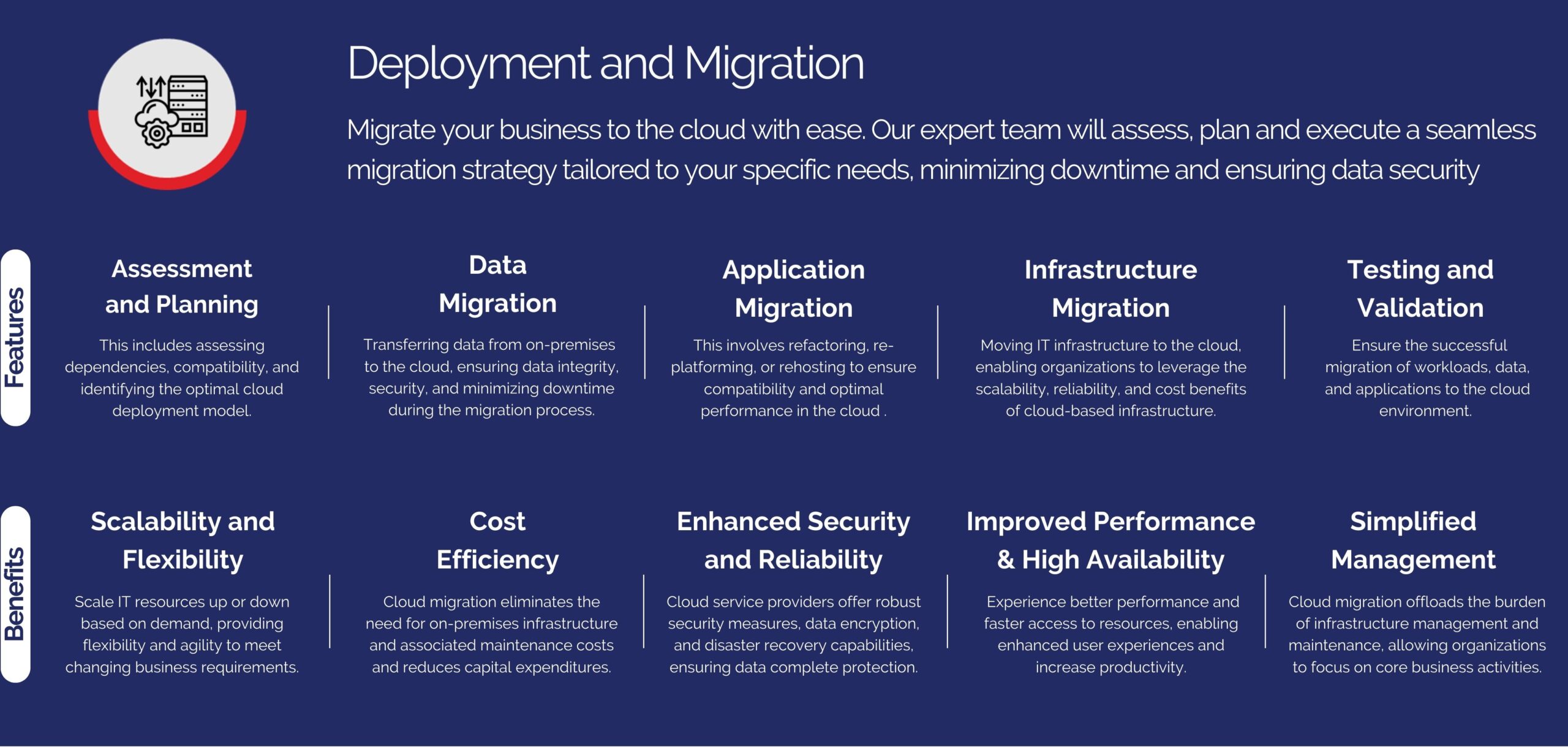
6. Secure Your Network –
- Protect your network by using firewalls and encryption. Firewalls act as a barrier between your internal network and external threats, while encryption ensures that data transmitted over the network is unreadable to unauthorized users. Use a Virtual Private Network (VPN) for remote access to enhance security further.
VAPT can be your 1st step towards a secure workplace...
Don't wait until a breach occurs, Take action now to protect your organization. Download our comprehensive guide on VAPT services.
Get Assessment
Learn more about how GBS Cybersecurity can help you safeguard your IT ecosystem and ensure regulatory compliance.
Secure your future today!
Cybersecurity Tips for SME Conti…
7. Backup Data Regularly –
- Regular data backups are crucial for recovering from cyber incidents like ransomware attacks. Ensure that backups are stored securely, preferably off site or in the cloud, and test them periodically to verify their effectiveness.
8. Develop an Incident Response Plan –
- Your organization’s contingency plan outlines the possible actions it will take in case of a cyber attack. It should include procedures for detecting, responding to, and recovering from incidents. Regularly review and update the plan to address new threats and changes in your business.
9. Limit Access to Sensitive Information –
- Implement the principle of least privilege by granting employees access only to the information and systems they need to perform their jobs. This minimizes the risk of insider threats and limits the damage that can be done if an account is compromised.
10. Monitor and Audit Systems –
- Continuously monitor your systems for unusual activity that could indicate a security breach. Regular audits of your security measures can help identify weaknesses and areas for improvement. Consider using automated tools to assist with monitoring and audits.
11. Use Secure Communication Channels –
- Ensure that sensitive information is transmitted securely by using encrypted communication channels. Avoid sending sensitive data over unsecured channels such as email. Instead, use secure messaging platforms or file-sharing services that offer encryption.
12. Conduct Regular Security Assessments –
- Regular security assessments, such as penetration testing and vulnerability scans, can help identify and address security weaknesses before they are exploited by attackers. Hire external experts if necessary to get an unbiased evaluation of your security posture.
13. Implement Physical Security Measures –
- Cybersecurity isn’t just about digital defenses. Ensure that physical access to your offices and servers is controlled and monitored. Use access cards, security cameras, and secure locks to prevent unauthorized physical access to your systems.
14. Stay Informed About Emerging Threats –
- Cyber threats are constantly evolving, so it’s essential to stay informed about the latest developments. Subscribe to cybersecurity news sources, participate in industry forums, and consider joining an Information Sharing and Analysis Center (ISAC) relevant to your industry.
15. Foster a Security Culture –
- Creating a culture of security within your organization is vital for long-term protection. Encourage employees to take ownership of their role in cybersecurity and recognize their contributions to maintaining a secure environment. Regularly communicate the importance of cybersecurity and celebrate successes in preventing attacks.
In Conclusion,
Cybersecurity is a continuous process that requires diligence and proactive measures. For SMEs, the stakes are high, as a single breach can have devastating consequences. By implementing these 15 essential Cybersecurity Tips for SME, you can significantly enhance your organization’s defenses and reduce the risk of falling victim to cyber-attacks.
Remember, the goal is not just to respond to threats but to anticipate and prevent them, ensuring the safety and security of your business in the digital landscape.
Follow us on social media to stay updated on the latest developments – Facebook & LinkedIn
GBS has now released a UAE Cybersecurity Report 2024 that you can Access Here – UAE Cybersecurity Report 2024
The State of the UAE Cybersecurity Report 2024 provides an in-depth analysis of the cyber threat landscape in the United Arab Emirates. As #cyberthreats continue to escalate globally, the #UAE faces unique challenges that necessitate robust defense mechanisms.
Our Previous blog Understanding the UAE Cybersecurity Landscape: Key Insights and Future Directions introduces the key findings of the #report and sets the stage for a deeper exploration of specific aspects in subsequent #blogs.
Access the Full State of Cybersecurity in the UAE – UAE Cybersecurity Report 2024 Today!