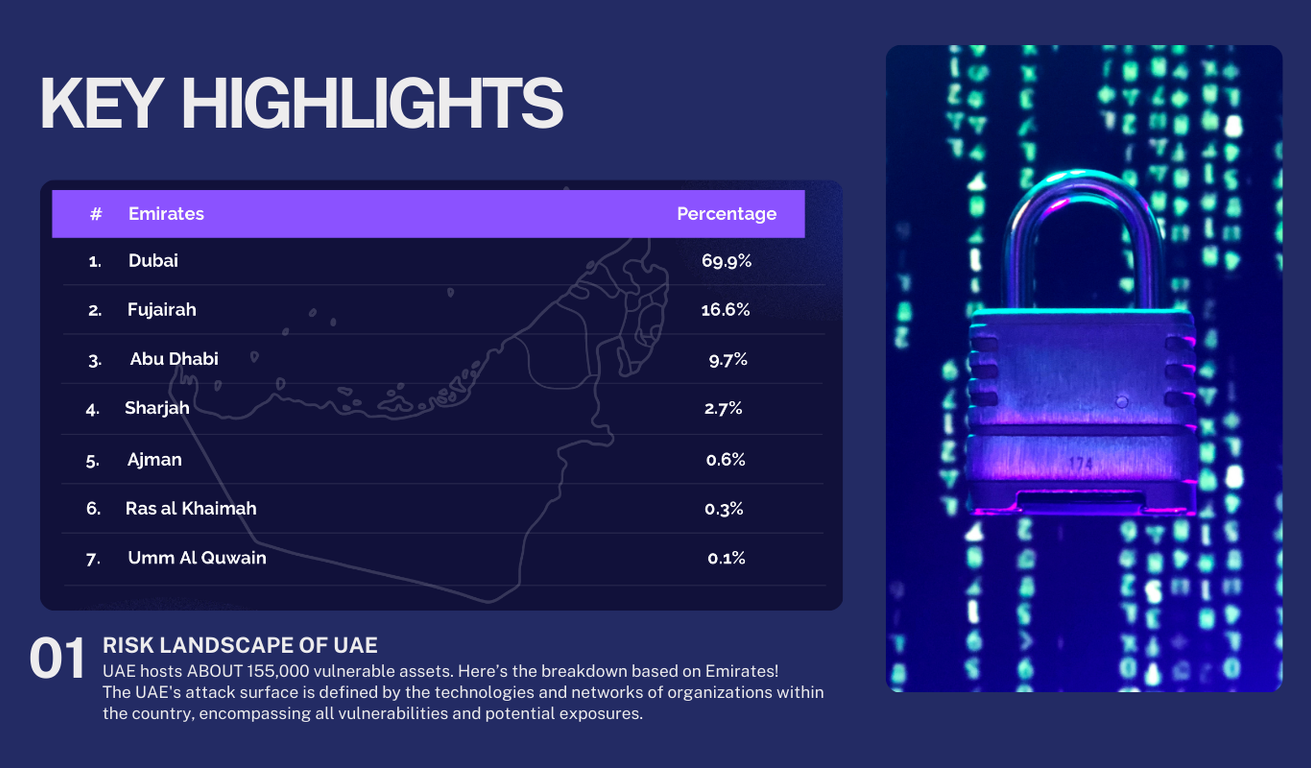
The cybersecurity threat landscape in the UAE isn’t just evolving — it’s accelerating.
While our 2024 Cybersecurity Report provided crucial insights into the challenges facing organizations, 2025 has brought new threats, sharper risks, and deeper regional divides.

Download Report
The UAE continues to lead in tech and innovation, but with progress comes growing cybersecurity risk.
This 2024 report offers a solid foundation—threat insights, risk trends, and strategic defenses.
Want the latest outlook? The 2025 edition is now available with updated data, AI threat analysis, and next-gen recommendations.
👉 Don’t miss it — Download the 2025 Report Here

Why Choose GBS?
GBS is a leading cyber security solutions provider in UAE offering comprehensive cybersecurity services. Our expertise in cyber threat analysis and prevention empowers organizations to maximize their data security while cutting down costs.
Whether you are looking for small business cyber security solutions or advanced systems for large-scale IT infrastructures, we have got you covered. Our cybersecurity managed services are ideal for organizations looking to seamlessly navigate the digital security landscape. By partnering with the industry-leading cybersecurity giants, we provide innovative solutions based on your requirements.
Know more here – About GBS
Guarding Against Cyber Threats: Our Comprehensive Protection
Unlock the potential of cybersecurity for your business, whether in Dubai, UAE, the Middle East, or globally. Choose GBS to get unparalleled flexibility, security, functionality, and innovative technologies. In today’s digital landscape, cyber threats come in various forms, each with its own strategy to breach your defenses. Know more about our Cybersecurity Solutions.
At our firm, we specialize in safeguarding against a range of malicious activities:
Malware
Malware is designed to cause damage or gain unauthorized access to computer systems or data. We provide protection against various types of viruses that may cause issues for you.
Ransomware
Ransomware attacks encrypt data or systems and demand payment for decryption. Our services include measures to identify and mitigate such attacks to improve your security.
Phishing
We offer solutions to combat phishing attacks. These attacks trick individuals into disclosing sensitive information such as passwords or financial details through deceptive means.
Insider Threat
Insider threat is cybersecurity risk originating from within a company. We create access control systems to limit access to confidential information, to prevent these threats.
Injection Attacks
We set up robust security measures to prevent the injection of malicious code into your software applications. This approach protects your digital assets against potential exploitation.
Zero-Day Exploits
Zero-day exploits target vulnerabilities in software or hardware that are unknown to the vendor or developers. We identify these issues and patch them to prevent potential cyberattacks.
Social Engineering
Social engineering attacks like Phishing manipulate people into giving away sensitive information. We train your employees to identify and mitigate such attacks to minimize the risk.
Password Attacks
Cybercriminals use various methods, from guessing passwords to keylogging and phishing, aiming to gain unauthorized access to secure accounts.