UAE Cybersecurity Report 2024- Cyber Threat Actors in 2024

Introduction – Understanding Cyber Threat Groups
Building on the insights from our first blog, this post focuses on the various cyber threat groups targeting the UAE. Understanding these groups’ motives and methods is crucial for developing effective defense strategies.
What This Blog Covers
- Overview of different cyber threat groups
- Specific tactics used by these groups
- How attack groups are targeting companies from various industries
- Preview of the next blog on legal compliance and outsourcing IT solutions
- Importance of proactive cybersecurity measures
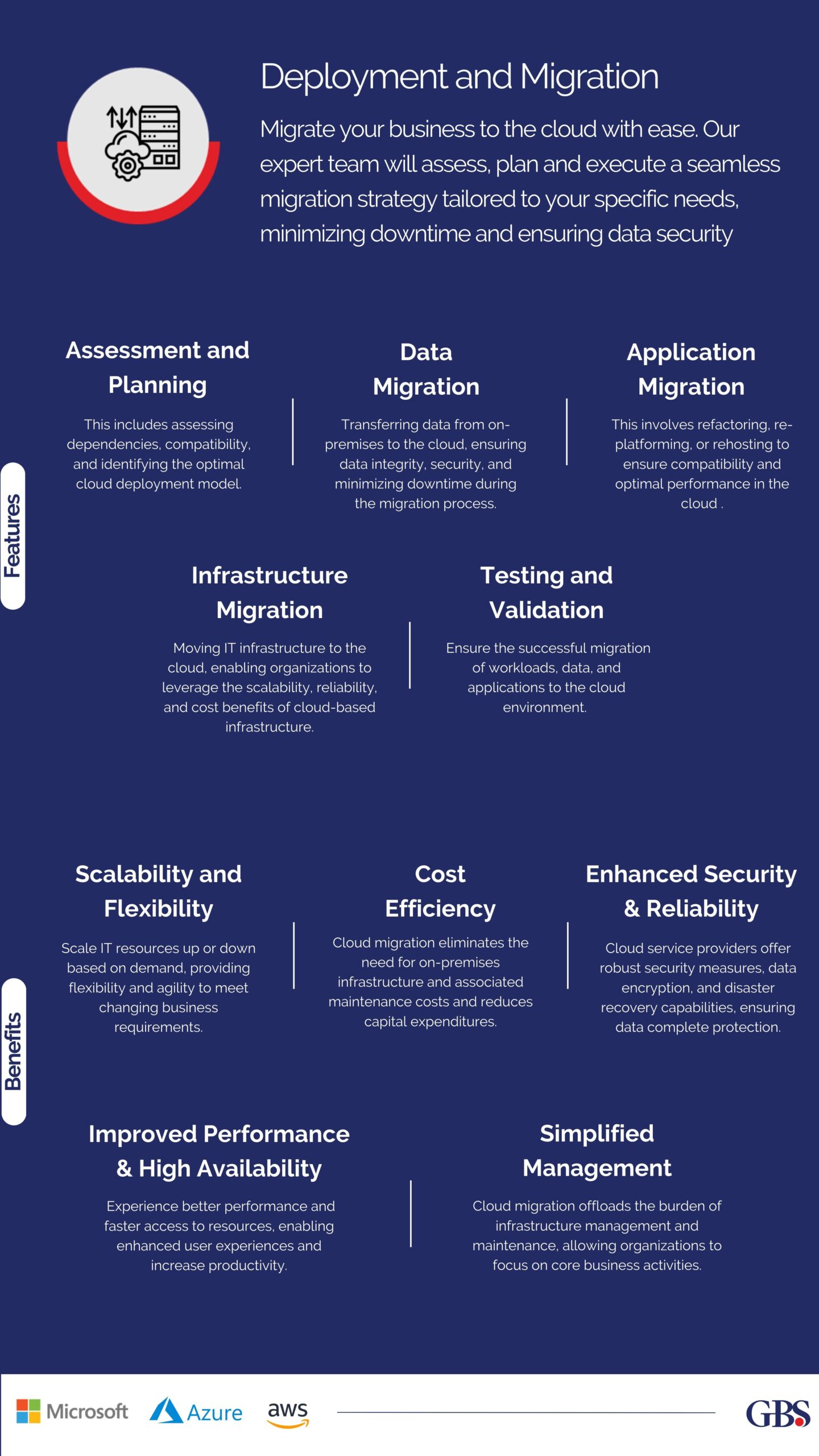
Different Attack Groups
Cyber threat groups vary in their motives and methods. The UAE faces threats from:
Nation-state Actors: These groups engage in cyber espionage and attacks to further their national interests. Notable examples include the North Korean-linked Lazarus Group, which has been active in the UAE. Nation-state actors target critical infrastructure, government institutions, and high-value commercial enterprises to gather intelligence and disrupt operations.
eCrime Organizations: These groups are financially motivated, employing tactics like ransomware and phishing to extort money from victims. Lockbit 3.0 and Cl0p are prominent actors in this category. eCrime organizations often use advanced malware and exploit vulnerabilities in software to gain access to systems and hold data hostage.
Hacktivists: Politically motivated groups like Anonymous Sudan conduct DDoS attacks to make political statements or disrupt services. Hacktivists leverage social media and other online platforms to coordinate their activities and amplify their impact. They often target government websites, financial institutions, and large corporations to draw attention to their causes.
Insider Threats: Employees or contractors with access to critical systems can pose significant risks, either intentionally or unintentionally. Insider threats can be difficult to detect and prevent, as they involve individuals who have legitimate access to sensitive information. Organizations need to implement stringent access controls and monitoring mechanisms to mitigate this risk.
How Attack Groups Target Companies
Industry Targets:
- Government and Energy Sectors: These sectors are frequently targeted due to their critical importance. Disruptions in these areas can have far-reaching consequences, making them attractive targets for cybercriminals.
- Information Technology: IT infrastructure is a common target due to its integral role in operations. Cybercriminals exploit vulnerabilities in software, hardware, and network configurations to gain unauthorized access and disrupt services.
Tactics:
- Phishing and Social Engineering: Used to gain access to sensitive information. Attackers craft convincing emails and messages to trick employees into revealing their credentials or clicking on malicious links.
- Ransomware: Encrypting data to demand ransom. Ransomware attacks often involve the use of encryption to lock critical files and systems, rendering them inaccessible until a ransom is paid.
- DDoS Attacks: Disrupting services to cause operational downtime. DDoS attacks flood networks with traffic, overwhelming servers and causing disruptions to online services and applications.
Preview of the Next Blog
The next blog will focus on the legal requirements for businesses in the UAE concerning cybersecurity. It will also discuss how outsourcing IT solutions can be an effective strategy for meeting these requirements and enhancing security. Understanding the legal landscape and leveraging external expertise can help organizations navigate the complexities of cybersecurity compliance and protection.
Conclusion
Every organization must understand the threat landscape to effectively protect its assets. By recognizing the different threat groups and their tactics, businesses can implement targeted defenses and reduce their vulnerability to attacks. Stay tuned for our next blog, where we will explore the legal requirements for cybersecurity in the UAE and how outsourcing IT solutions can help businesses comply with regulations and enhance their security posture.
Curious to Learn More about the Solution? Click Here to Receive the Complete Solution Brief – Solution Brief
Follow us on social media to stay update on latest developments – Facebook & Linkedin